Does it ever seem like your small business is overwhelmed with data? This is a very common phenomenon. The digital world has transformed how small businesses operate. We now have an overwhelming volume of information to manage employee records, contracts, logs, financial statements, not to mention customer emails and backups. A study by PR Newswire […]
Your office thermostat, conference room speaker, and smart badge reader are convenient, but they’re also doors into your network. With more devices than ever in play, keeping track can be tough, and it only takes one weak link to put your entire system at risk. That’s why smart IT solutions matter now more than ever. […]
Is your team constantly reinventing the wheel? It might be time to build a smarter way to share what you already know. Every small business runs on shared knowledge. How things work, what’s been tried, and what actually delivers. But when that knowledge isn’t documented, mistakes repeat, and progress slows. Inefficient knowledge sharing impacts businesses […]
Nothing disrupts your workday quite like unreliable Wi-Fi. One moment everything’s running smoothly, and the next, video calls freeze, files won’t upload, and the team struggles to meet deadlines because everything’s slowed down. Being stuck in this situation is exhausting, killing productivity, and impacting the entire business. When slowdowns start happening regularly, frustration quickly builds. […]
In the past, teams relied on sticky notes and endless email threads to manage tasks. But with today’s hybrid work environments and fast-moving deadlines, that approach just doesn’t cut it anymore. Effective project management is now essential to stay on track and ahead. According to McKinsey, the average worker spends 28% of their week managing […]
Without realizing it, technology can drain your business budget. One day, everything seems manageable, and the next, you’re left wondering where all these unexpected costs are coming from. Expenses pile up quickly and become tough to track. Whoever said running a business would be easy? Here’s the good news: you don’t need to spend thousands […]
Nobody builds a house on a weak foundation, so why operate your business based on unreliable data? According to research, bad data costs US firms over $3 trillion every year, and roughly 40% of company goals fail as a result of inaccurate information. Data is everywhere, and if you are not utilizing it to your […]
Let’s be honest, operating a small or medium-sized business requires wearing multiple hats. From chasing approvals to manually updating spreadsheets, it’s easy for your team to get stuck doing time-consuming tasks that drag down productivity. That’s where smart IT solutions come in, and one of the most effective tools available today is Microsoft Power Automate. […]
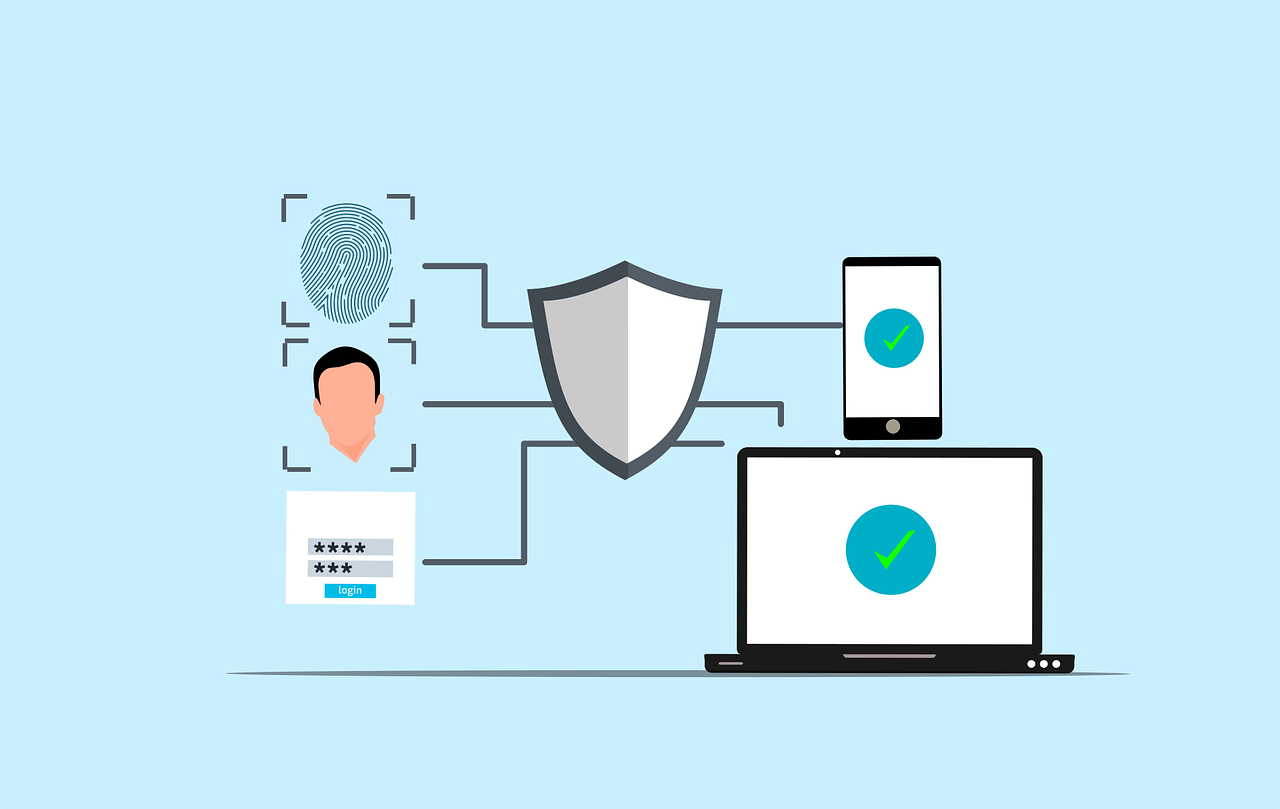
Have you ever wondered how vulnerable your business is to cyberattacks? According to recent reports, nearly 43% of cyberattacks target small businesses, often exploiting weak security measures. One of the most overlooked yet highly effective ways to protect your company is through Multi-Factor Authentication (MFA). This extra layer of security makes it significantly harder for […]
Personal data protection is more important than ever in this digital world. The dark web is a secret part of the internet that is very dangerous because it is often used for illegal things like selling personal information. Because the dark web is decentralized and private, it is very hard to get rid of data […]